Strata Logging Service | Send Palo Alto logs to an AWS S3 bucket
Prerequisites
Once the IAM Policy is selected click on Next and again click on Create Role to finish the IAM role creation.
@Strata Logging Service
Once these values are entered then click on Test Connection. If test is succesful, then go to next step
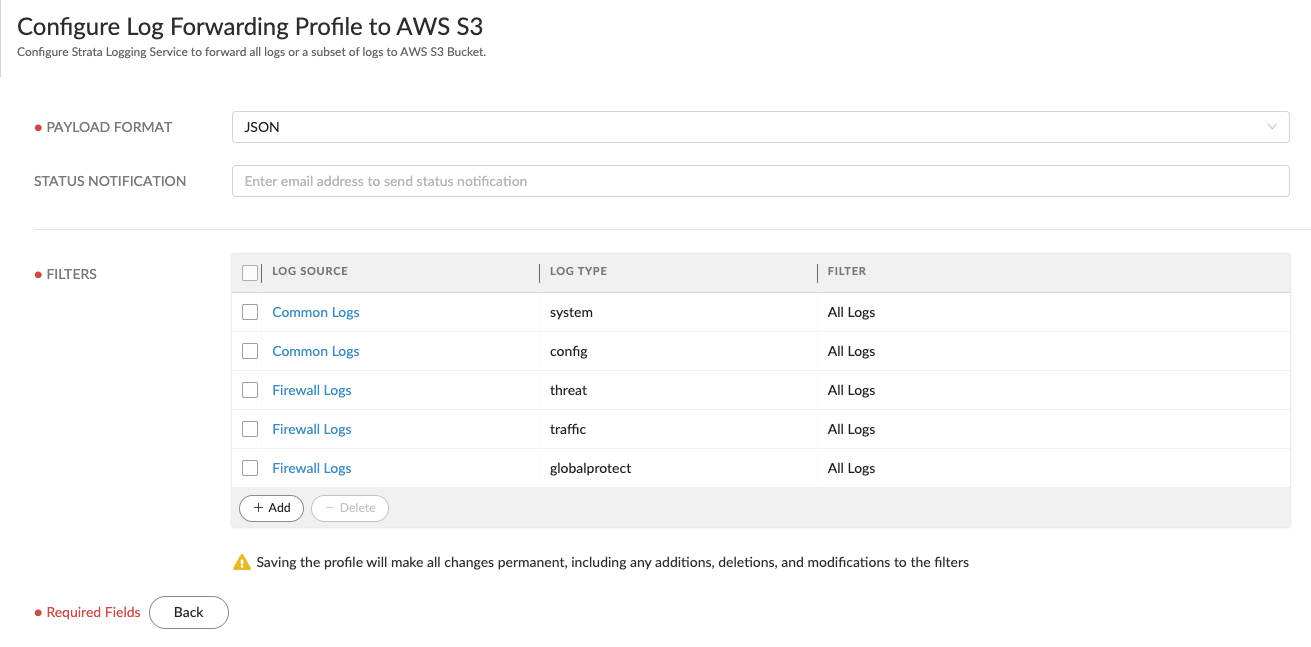
Select all your desired palo alto log types in filter in the final step (traffic logs, threat logs, system logs, etc). Click Save to Finish.
If all the steps are made correctly then we should be able to see this on SLS screen:
1. Have 1 or multiple Palo Alto Firewalls onboarded to Strata Cloud Manager or sending Palo Alto logs directly to Strata Logging Service.
2. Have access to Strata Logging Service / Strata Cloud Manager console.
3. Have access to an AWS Console
How to send Palo Alto logs to an AWS S3 bucket
@AWS
1. Create a new S3 bucket. We will call it palo-alto-logs.
Take note of the AWS region (us-central-1, eu-central-1, etc) this will be required on a later step.
Also for security, kindly enable Block all public access in the S3 Bucket.
It is not required to create an ACL so you can disable this setting.
2. Create a new IAM role. We will call it SLS_to_S3_access_role.
During the creation of the IAM role, you need to select AWS Account > Another AWS Account > Enter the Account ID of Strata Logging Service. This can be obtained when creating a new S3 bucket profile in Strata Logging Service, specifically here:
Also for security, kindly enable Block all public access in the S3 Bucket.
It is not required to create an ACL so you can disable this setting.
2. Create a new IAM role. We will call it SLS_to_S3_access_role.
During the creation of the IAM role, you need to select AWS Account > Another AWS Account > Enter the Account ID of Strata Logging Service. This can be obtained when creating a new S3 bucket profile in Strata Logging Service, specifically here:
Once the AWS Account ID it is obtained, we will paste it under Account id and also an External ID value will be defined afterwards. The External ID is like Secret value that is defined in both SLS and AWS and it is a random and arbitrary value. We click on Next.
On next step, we need to attach an IAM policy to the IAM role. Before the IAM role creation we actually created an IAM Policy that grants PUT access (basically write only access) to my s3 bucket.
Once the IAM Policy is selected click on Next and again click on Create Role to finish the IAM role creation.
@Strata Logging Service
1. Go to Strata Logging Service > Log Forwarding > AWS S3 > Click on + to add a new S3 profile
Now enter the following required values:
Now enter the following required values:
- Name: {THIS_IS_RANDOM}
- AWS Bucket Name: palo-alto-logs (this has to match with the actual s3 bucket name)
- AWS Region: {S3_BUCKET_ASSIGNED_REGION} (examples: us-central-1, eu-central-1, etc)
- AWS Bucket Name: palo-alto-logs (this has to match with the actual s3 bucket name)
- AWS Region: {S3_BUCKET_ASSIGNED_REGION} (examples: us-central-1, eu-central-1, etc)
- IAM ROLE ARN: Should look like this -> arn:aws:iam::xxxxxxxxxxxrole/SLS_to_S3_access_role
- EXTERNAL ID: {RANDOM_VALUE_ASSIGNED_IN_IAM_ROLE_ENTITY_POLICY}
- EXTERNAL ID: {RANDOM_VALUE_ASSIGNED_IN_IAM_ROLE_ENTITY_POLICY}
Once these values are entered then click on Test Connection. If test is succesful, then go to next step
Select all your desired palo alto log types in filter in the final step (traffic logs, threat logs, system logs, etc). Click Save to Finish.
If all the steps are made correctly then we should be able to see this on SLS screen:






Comentarios
Publicar un comentario